EW71 VLAN FIREWARE(DL FILE) : DOWNLOAD HERE!
🛡️ Mastering Network Segmentation: An In-Depth Guide to Virtual Local Area Networks (VLANs)
A modern network, whether in a large enterprise or an advanced home office, requires more than simple connectivity; it demands intelligent segmentation. Virtual Local Area Networks (VLANs) are the foundational technology that allows network administrators to logically partition a physical network infrastructure, drastically improving security, scalability, and performance.
I. The Technical Core of VLANs: Tagging and Isolation
While traditional Local Area Networks (LANs) group devices based solely on their physical connection to a switch, a VLAN groups devices based on logical criteria (e.g., department, security level, or function).
The IEEE 802.1Q Standard
The critical mechanism enabling this segmentation is the IEEE 802.1Q protocol. When a frame (a unit of data) is sent between switches on a connection known as a trunk port, the transmitting switch inserts a special 4-byte header into the Ethernet frame. This header contains the VLAN ID (VID), a 12-bit identifier that specifies which VLAN the frame belongs to, allowing for $2^{12} = 4096$ possible unique VLANs.
This tagging mechanism is what allows multiple logical networks to travel across a single physical cable, or trunk link, without interference.
Segmenting Broadcast Domains
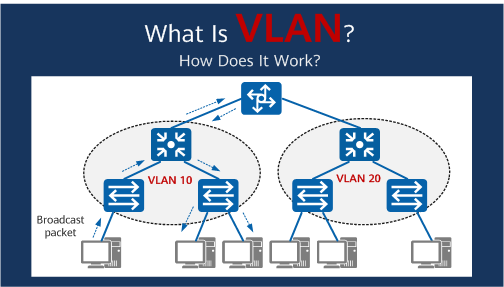
The most significant performance benefit of a VLAN is the isolation of broadcast domains.
In a standard, flat network, a broadcast storm (where one device sends a message to all other devices, such as an ARP request) affects the entire network, consuming bandwidth and processing power on every attached device.
By implementing VLANs, the switch confines this broadcast traffic strictly to devices that share the same VLAN ID. This segmentation significantly reduces unnecessary traffic, leading to lower latency and higher overall throughput on the network.
II. Strategic Benefits in Modern Networking
VLANs are not just a technical feature; they are a critical component of network strategy across security, flexibility, and management.
1. Robust Security Enhancement
VLANs enforce the principle of least privilege by separating network traffic. Consider these practical examples:
IoT Isolation: Place all Internet of Things (IoT) devices (smart speakers, security cameras) into a dedicated "IoT VLAN." If a single IoT device is compromised, the attacker is contained within that VLAN and cannot easily access sensitive resources on the "Server VLAN" or "Employee Data VLAN."
Guest Access: Public or guest Wi-Fi traffic is isolated to a "Guest VLAN" that has no access to internal corporate resources, minimizing risk to intellectual property and internal systems.
2. Operational Flexibility and Mobility
VLANs streamline network management when devices or users relocate.
In a large office, if an employee moves from the Marketing Department to the Engineering Department, the network access and security policies associated with their user profile are tied to the Engineering VLAN. The administrator simply changes the switch port's assignment (or uses dynamic VLAN assignment via 802.1X) to the Engineering VLAN, and the user instantly gains the correct access rights, eliminating the need for IP address changes or physical cable runs.
III. Advanced Implementation: Inter-VLAN Routing and Management
While VLANs provide separation, communication between these isolated networks is often necessary. This requires Inter-VLAN Routing.
The Need for Layer 3 (L3) Devices
Because VLANs exist at Layer 2 (Data Link Layer), communication between them requires a Layer 3 (Network Layer) device—a router or a Layer 3 managed switch.
The most common technique is Router-on-a-Stick:
A single physical link between the Layer 2 switch and the router is configured as an 802.1Q trunk.
The router's single physical interface is logically divided into multiple sub-interfaces, with each sub-interface configured to handle the traffic for a specific VLAN.
When a device in VLAN 10 needs to talk to a device in VLAN 20, the frame is sent to the router's VLAN 10 sub-interface. The router de-encapsulates the frame, performs the Layer 3 routing lookup, applies any necessary Access Control Lists (ACLs), and then re-encapsulates the packet into a new frame, tagging it with VLAN 20, and sending it back out the trunk.
This method allows for controlled and auditable communication between segments, providing a central point for policy enforcement that is vital for modern security compliance.
VLAN Management Strategies
VLAN configuration typically happens at the switch level and involves defining three types of ports:
Access Ports: Used for end-user devices (PCs, printers, IP phones). They belong to only one VLAN, and any untagged traffic entering the port is automatically assigned to that VLAN.
Trunk Ports: Used to connect switches or switches to routers. They carry traffic for multiple VLANs and require 802.1Q tagging.
Voice VLAN: A specialized feature that automatically assigns an IP phone and its connected computer to two separate VLANs (Voice and Data) on the same port, prioritizing the voice traffic for Quality of Service (QoS).
In essence, VLANs are the essential framework for building networks that are not only high-performing and flexible but fundamentally secure and scalable enough to meet the demands of tomorrow's digital infrastructure.
WHAT IS COMFAST?
📡 Deep Dive Review: The COMFAST CF-EW71 as a Cost-Effective Outdoor Wi-Fi Solution
COMFAST has established itself as a major provider of cost-effective, feature-rich networking equipment, bridging the gap between basic consumer routers and expensive enterprise solutions. The COMFAST CF-EW71 Wireless Access Point (AP) is a prime example, specifically designed for robust, long-range outdoor Wi-Fi coverage and essential in micro-enterprise models like the Piso Wi-Fi business popular in the Philippines.
I. Core Specifications and Design Analysis
The CF-EW71 is engineered to withstand harsh environments while delivering a strong 2.4 GHz Wi-Fi signal. Understanding its hardware is crucial for deployment strategy.
Key Hardware Features
| Specification | Detail | Practical Implication |
| Model | CF-EW71 (or V2) | Outdoor High Power AP |
| Wi-Fi Standard | 802.11b/g/n (2.4 GHz) | 300 Mbps maximum data rate |
| Chipset | Qualcomm QCA9531 | Stable performance; proven platform |
| Antennas | Two external 5dBi omnidirectional | 360° coverage for wide areas |
| Power Supply | 48V PoE (802.3af/at standard) | Allows power and data over a single Ethernet cable (up to 100m) |
| Protection Rating | IP66 Waterproof/Dustproof | Durable in all-weather outdoor deployment |
| Client Capacity | Supports 50+ concurrent users | Ideal for high-density public access |
The Significance of Power over Ethernet (PoE)
The support for PoE is a major factor in the device's utility.
II. Deployment Scenarios and Application Mastery
The CF-EW71’s high-power output and rugged design make it versatile for several demanding applications.
1. Piso Wi-Fi / Vendo Machine Integration
The CF-EW71 is a staple in the Piso Wi-Fi ecosystem.
Configuration Mode: The device is typically set up in Access Point (AP) mode, connecting to a main gateway or a Piso Wi-Fi timer box via its LAN port.
6 Performance: The high-power amplifier (500mW / 27dBm) ensures that users can connect from a greater distance, maximizing the coverage and potential customer base for the vendor.
7
2. Long-Range Repeater/Bridge for Coverage Gaps
Beyond AP mode, the CF-EW71 can be configured as a Wireless Repeater or Bridge.
Repeater Mode: Used to extend the range of an existing indoor Wi-Fi network into a backyard, common area, or outdoor parking lot. While convenient, this mode halves the effective bandwidth.
Bridge Mode: Used to wirelessly link two distant locations (e.g., two buildings or two houses) where running a cable is impractical. This requires two CF-EW71 units to establish a dedicated Point-to-Point link.
III. Configuration and Advanced Features
The device includes a web-based management interface, simplifying configuration even for non-technical users.
Channel Optimization: In crowded 2.4 GHz environments, the device's ability to automatically select an optimal, non-overlapping channel (1, 6, or 11) is essential for mitigating Co-Channel Interference and maintaining stable throughput.
10 SSID and VLAN Tagging: For businesses, the CF-EW71 often supports the creation of multiple SSIDs (e.g., one for staff, one for public access). On compatible models, these SSIDs can be mapped to different VLAN IDs (IEEE 802.1Q tagging) to ensure traffic segmentation and network security.
11 This prevents public Wi-Fi users from accessing the internal business network.
In summary, the COMFAST CF-EW71 provides a compelling blend of enterprise-grade features (PoE, IP66 rating, high client capacity) at a budget-friendly price point, making it an excellent subject for a detailed technical review aimed at a wide audience of small business owners and network enthusiasts.